In 2011, just two years after Bitcoin was launched, British-Iranian anarchist developer Amir Taakia and a group of open-source coders created an alternative to Bitcoin Core – the original and still the most popular way of connecting to the Bitcoin network.
That alternative piece of software, branded Libbitcoin, has now evolved into a comprehensive suite of tools – a library – for critical functions like communicating with the Bitcoin blockchain and generating cryptographic keys.
It was even featured in Bitcoin educator Andreas Antonopoulos’s popular and arguably canonical book Mastering Bitcoin.
But after roughly $900,000 disappeared from various user wallets over the past few months, Libbitcoin, once presumed secure, has turned out to be unsafe.
Here’s how the latest saga unfolded, according to a report on milksad.info, which details the findings of Distrust, the security firm that discovered the vulnerability in July, assisted by a group of independent contributors.
At some point in May, hackers began secretly stealing funds from unsuspecting users after discovering an obscure vulnerability in a number of wallets generated by the Libbitcoin explorer, called BX.
The vulnerability was dubbed “Milk Sad” because “milk” and “sad” were the first two words in a wallet-recovery seed phrase generated by the vulnerability, the report states.
The most significant heist – 29.65 bitcoin (BTC) worth about $870,000 at current rates – took place July 12. Distrust says a total of at least $900,000 was stolen across multiple blockchains, including from some of the roughly 2,600 bitcoin wallets affected by the vulnerability.
Hardware wallets like Trezor and Ledger seem to have been unscathed, but there are still a number of wallets at risk, and the full extent of money stolen is “yet to be determined,” according to an Aug. 8 tweet by Anton Livaja, a member of the Distrust team.
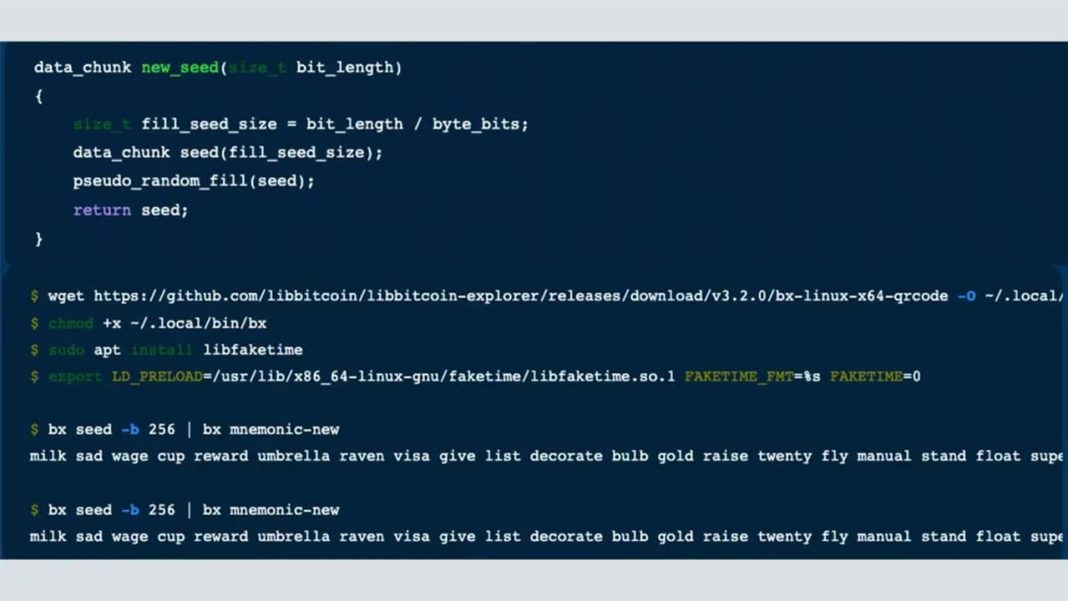
BX comes with a text command called “bx seed” that uses the clock on a developer’s computer to produce a seed phrase for creating a wallet.
Crypto software provides random combinations of 12 to 24 words or seed phrases to users who want to “recover” or regain access to their wallets in the case of accidental loss.
But when using BX, the resultant phrase turns out to be insufficiently random. According to the report, “a decent gaming PC can do a brute-force search,” or guess all possible word combinations for a user’s seed phrase, “in less than a day.”
“Think of this as securing your online bank account with a password manager that creates a long random password,” the report states. “But it often creates the same passwords for every user. Malicious people have figured this out and drained funds on any account they can find.”
Ethereum, Zcash, Solana, Dogecoin affected
Milk Sad is not restricted to Bitcoin. Ethereum, Zcash, Solana and even Dogecoin are among the list of eight blockchains affected. Similar but not identical vulnerabilities have been detected in Cake Wallet and Trust Wallet, both multi-chain wallet apps.
Typically, seed phrases are created using a generator capable of producing a set or “key space” with a dizzying number of unique word combinations represented by the exponent of a binary digit or “bit” – essentially, the number two raised to the power of 128, 192 or 256.
BX has a paltry 32-bit key space which can only yield about 4.3 billion unique word combinations. “That’s not as many combinations as it sounds,” according to the report.
Eric Voskuil, BX’s lead developer, admitted that the seed generator was indeed insecure, but insisted there was no bug in the software, arguing that the bx seed text command had been misused. He tweeted a screenshot of the application’s GitHub documentation that warns developers of the vulnerability.
“This is not a bug in BX or Libbitcoin,” Voskuil tweeted. “It is reckless wallet development.”
Several cryptographers in the Bitcoin community begged to differ.
“The case is crystal-clear,” tweeted Tim Ruffing, cryptographer at Bitcoin infrastructure firm Blockstream. “It’s your bug, period.”